Face the facts – your organisation will be breached
Face the facts – your organisation will be breached
It’s simple: cyber-security isn’t working. Too many companies are being breached and governments globally are recognising the need to invest heavily to protect vital services and infrastructure. When the most fiscally prudent UK Chancellor of the Exchequer in a generation stumps up an additional £1.9bn to combat the cyber-security threat, reality starts to bite – organisations of every size need to do more to safeguard operations.
other problem is that the way in which cyber-terrorists are gaining access to networks has changed. Today, an esti- mated 95% of breaches occur as a result of a user being compromised, usually through a phishing attack.2
Today’s defence-in-depth security models are not completely flawed, but they are, perhaps, naïve. When firewalls are being easily bypassed and it’s tak- ing upwards of six months to detect a breach, the reliance on traditional access control, threat detection and threat pro-
tection is clearly inadequate.1
Announcing a breach is bad enough; no CEO wants to admit to the media that the company has no idea whether a breach is catastrophic or insignificant, or that it has no idea how long the threat lay undetected. Organisations need to add another layer – breach containment. It is only by recognising that a breach has already occurred and containing that breach within a defined and secure seg- ment that an organisation can avoid the damaging system-wide events that are becoming a daily occurrence.
It is time to face up to the futility of breach detection and protection alone. Organisations must make a change to avoid the fate of the enterprises that have recently hit the hacking headlines.
Security agenda
these technologies are not enough.
The defence-in-depth security model that encompasses firewalls and anti-virus, file integrity monitoring and access con- trol is essential – without it, businesses would lose vital sensitive data and essen- tial infrastructure would be compro- mised. However, from the recent events at TalkTalk onwards, it is clear that the model as it stands today is failing.
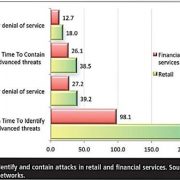
Yet according to research conducted by the Ponemon Institute on behalf of Arbor Networks, once a data breach occurs, it takes an average of 98 days for financial services companies to detect intrusion on their networks and 197 days in retail. That is upwards of six months for hackers to conduct surveil- lance and steal data undetected. The
“It takes an average of 98 days for financial services companies to detect intrusion on their networks and 197 days in retail”
The lesson for enterprise IT managers is this: your applications are now only as safe as the least secure user or external party to whom you grant access. When an attacker uses authenticated credentials to access the network, a firewall is useless. The assump- tion that a user on an internal network can be trusted is obsolete. Firewalls cannot block this attack vector because hackers compromise one user and then can move through the enterprise to any sensitive application.
The threat landscape has evolved again and weaknesses are being laid bare on a near-daily basis. The truth is that while considerable investment in threat detection and threat prevention is essential to deter the vast majority of attempts to compro- mise or hack an organisation’s network,
Time in days to identify and contain attacks in retail and financial services. Source: Ponemon/Arbor Networks.
The one method that does work against these attacks is application seg- mentation, which applies strict access controls to limit users to only the appli- cations they need to access for their jobs. That should be applied to users both inside and outside the enterprise, including users on the previously trusted internal networks. Then, if a user is
compromised, the worst that can happen is that the hacker can get access to the small subset of applications that the user can access. It is only once the attacker actually attempts to elevate or escalate that user’s privileges to access sensitive or critical data that an organisation has
a chance of detecting the threat. Threat detection and protection technologies are clearly failing to deliver a complete cyber-security solution.
A breach will happen
To achieve this breach containment model, companies need to think differ- ently about security architecture design. Breaches are occurring all the time and organisations need to accept that it is more than likely that a breach has either already taken place or is currently under- way within their environment and that this can and will happen without any notification.
With that understanding comes a recognition that the objective is now to contain any breach – whether known or unknown – and minimise any risk of it becoming system-wide. The emphasis
is no longer solely on building walls to keep people out but on containing that breach and minimising the extent of it by building (fire) doors between differ- ent parts of the infrastructure.
After accepted the premise, the chal- lenge is to then understand the best way to break down the infrastructure into manageable segments of risk. For most IT experts the logical approach to creating microsegments would appear to be at the network layer: however, this has massive limitations, not least the proven frailty of the network infrastructure. Every time a change is made to an access control list,
IP address or subnet, there is a real risk of opening the door to bypassing the firewall. Furthermore, in a cloud- and
mobile-enabled environment where net- works are often outside an organisation’s control, it is simply not possible to deploy a robust end-to-end strategy.
Users and applications
Companies need to step back and look at this from a true business perspective
and focus on users and applications. Who needs access to what data? Building on the existing policies for user access and identity management, organisations can use cryptographic segmentation to ensure that only privileged users have access to privileged applications or information. Each cryptographic domain has its own encryption key, making it impossible for a hacker to move from one compromised domain or segment into another, there- fore preventing the lateral movement
that leads to many breaches – it is simply not possible to escalate user privileges to access sensitive or critical data.
With this approach, an organisation can narrow the scope of a breach to a small, contained area rather than system- wide and, critically, do so in a way that removes the need to build new security policies into the network infrastructure. Furthermore, as and when a breach is a detected, the segmentation policy means that an organisation has immediate visibility into the extent of the breach
- enabling targeted rather than system- wide lock-down and a far more confi- dent and measured response to media, shareholders and
New mind-set
This is without doubt a huge mind- set change. While organisations have worked hard on creating robust defence-in-depth security strategies, with security experts globally now recommending a containment policy based on clearly defined infrastructure segments, it is clearly time to make a change. However, those organisations simply opting to impose containment at the network level are failing to rec- ognise the true threat landscape: a reli- ance on network-based controls adds
- not mitigates – risk. It is simply too easy to bypass these
It is only by following a user- and application-based segmentation approach that an organisation can truly address the heart of the matter: the breach is contained within one specific segment. The hacker cannot bypass the cryptographic key to escalate privileges and gain access to data that is only available to users within a different cryptographic segment. The organisa- tion knows immediately the extent
of the breach and the data, users and applications affected.
This latter point is key: no CEO wants to be in the position of Baroness Dido Harding, the CEO of TalkTalk, who had to admit that the company did not know the extent of the breach or the number of customers whose data had been compromised. An effec- tive breach-containment strategy both minimises the extent of the breach and provides immediate clarity of risk to shareholders and customers.
Adding another layer to an already complex defence-in-depth security strategy may seem onerous but, as George Osborne said when he was UK Chancellor of the Exchequer: “Getting cyber-security right requires new thinking.”
About the author
Paul German is VP EMEA for Certes Networks. He has more than 18 years of experience and was most recently VP/GM EMEA for Sipera Systems, an IT security solutions company sold to Avaya in 2011. In addition, German has broad experience, having held key roles with Cisco, Siemens Network Systems and Lehman Brothers. He holds a Bachelor of Science honours degree from Brunel University, London.
References
- Osborne, ‘Most companies take over six months to detect data breaches’. ZDNet, 19 May 2015. Accessed Aug 2016. www.zdnet. com/article/businesses-take-over-six- months-to-detect-data-breaches/.
-
‘2015 Verizon Data Breach Investigation Report’. Accessed Aug 2016. http://news. verizonenterprise.com/2015/04/2015- data-breach-report-info/.