Dangerous skills gap leaves organisations vulnerable
Dangerous skills gap leaves organisations vulnerable
These days, not only are businesses having to contend with increasingly sophis- ticated attacks on data, they are also facing a serious skills gap within the pro- fessions that should be responsible for preventing these attacks. In the security landscape, this role can have a number of job titles – security engineer, security analyst, ethical hacker, penetration tester, security researcher. But they all have one goal – to identify and report on vulnerabilities within security systems.
Stark contrast
White hat hackers stand in stark con- trast to the malicious black hat hackers, who intentionally cause damage to their
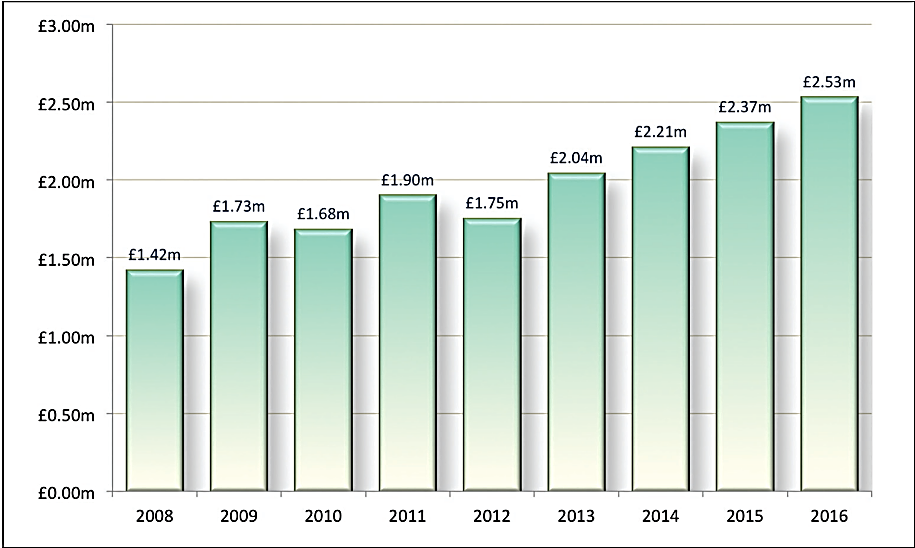
A report from PwC found that 90% of large organisations had suffered an infor- mation security breach in 2015.1 What’s more, 69% were attacked by a mali- cious ‘outsider’ in the past year. Clearly, it is no longer simply a matter of ‘if’ a company will suffer a data breach, but ‘when’. The Ponemon Institute’s ‘2016 Cost of a Data Breach’ report found that on average a data breach will cost an organisation £2.53m, with most cases still caused by criminal and malicious attacks.2 The enormous financial burden can be attributed to a number of factors, including falling share prices, lawsuit payouts, regulatory fines, damage to reputation and employee layoffs.
The role of white hat hackers
To protect against the serious conse- quences of a data breach, many compa- nies are turning to ethical hackers (or white hat hackers as they’re otherwise known) to help identify vulnerabilities before they become a target for malicious cyber-attacks. On the colour spectrum
of hackers, ‘white hats’ are the ethically minded people who are employed to systematically undertake an attack on an organisation’s infrastructure and informa- tion systems, but only with explicit per- mission. By doing this, they can find and test any weaknesses or areas that mali- cious hackers could potentially exploit.
While identifying vulnerabilities is an
integral part of the white hat hacker’s role, knowing how to defend and protect these weak points is just as important. Therefore, white hat hackers also engage in red-team/blue-team style simulations. This process involves the hackers taking turns to attack and defend an organisa- tion’s information systems and acts as
a means of reviewing both the gaps in security and the ways in which they need to be addressed.
White hat hackers will often hold industry accreditations – for example, the Certified Ethical Hacker (CEH) cer- tification offered by the EC-Council, or Offensive Security Certified Professional (OSCP) certification. These courses look at cyber-security in relation to hacking and how security professionals can use this mind-set to understand the weak- nesses within organisations. The OSCP requires students to demonstrate practi- cal penetration-testing skills by getting them to successfully break into working machines in a controlled lab environ- ment. When undertaking the CEH course, students learn about the typical ways to exploit weaknesses, the vulner- abilities and their countermeasures, as well as how to master penetration test- ing, social engineering and footprint- ing. On top of the CEH accreditation, the EC-Council also offers certifica- tions, including Computer Hacking Forensic Investigator (CHFI), Certified Security Analyst (ECSA) and Licensed Penetration Tester (LPT).
targets through illegal online activities. It is the difference in motivation that truly sets them apart. Black hat hackers can be broken down into a number of categories – cyber-criminals, cyber-spies, hacktivists and cyber-terrorists – and are driven by varying motivations including bragging rights, money, revenge, valu-
able data, media attention or even just for their own amusement. White hat hack- ers are also tasked with monitoring the activity of black hat hackers and tackling the commoditisation of security vulner- abilities. This entails keeping an eye out for the latest scripts that are being created and sold on the dark web. These scripts are bought, sold and exchanged by ‘script kiddies’, who use the code to break into the information systems of organisations.
Between the white and black hat hackers lies a third colour category – grey hat. These can often be the most dangerous, especially when it comes to trying to recruit ethical hackers to join an organisation’s security team. This is because some ‘grey hats’ are classified as black hat hackers, masquerading as white hat hackers. As such, companies look- ing to hire a white hat hacker should treat any above-average or stand-out job application with suspicion, and be on the lookout for red flags to indicate the person is acting with malicious intent. In some cases, job applications are from black hat hackers who have realised a company is vulnerable, and are looking for the opportunity to gain access to the
The average cost of a data breach for UK organisations. Source: Ponemon Institute/IBM.
often turn to a process called ‘bug boun- ty programmes’. These programmes see businesses invite the security community to attempt to hack the organisation’s systems, and then report back on their findings. This process of ‘crowdsourc- ing’ hacking offers security professionals, students and even just simple security enthusiasts the opportunity to ethically hack a company – something which would normally see them being arrested and charged with illegal activity.
While it may seem unorthodox, the bug bounty method of penetration test- ing can be a win-win situation for both the company and the hackers them- selves. The company gets the economic advantage of only having to pay when a
system at a later date by creating ‘time bomb’ backdoors or plant viruses that will exploit the data stored internally.
“Companies looking to hire a white hat hacker should treat any above-average or stand-out job application with suspicion, and be on the lookout for red flags to indicate the person is acting with malicious intent”
One way to ensure that grey hats don’t become part of the security team is to carry out background security and credit checks during the recruit- ment process, as well as thoroughly researching previous job placements. This means more than just phoning the reference numbers on the resume. Credit checks, while not a failsafe solu- tion, will help identify people with an unusually large amount of money that cannot be accounted for through nor- mal means. This often indicates they have gained this money through illegal activity, such as hacking. Those with poor credit, or multiple court judg-ments (CCJs), could also be susceptible to social engineering or bribery.
The skills gap
Though it is clear that penetration test- ing and ethical hacking is an integral part of protecting a company from a data breach, employees with the neces-
sary skills are some of the hardest to come by. The cyber-security market is suffering a severe workforce shortage – worldwide there are approximately two million jobs that are currently vacant. This is leaving companies dangerously exposed to attacks on sensitive data.
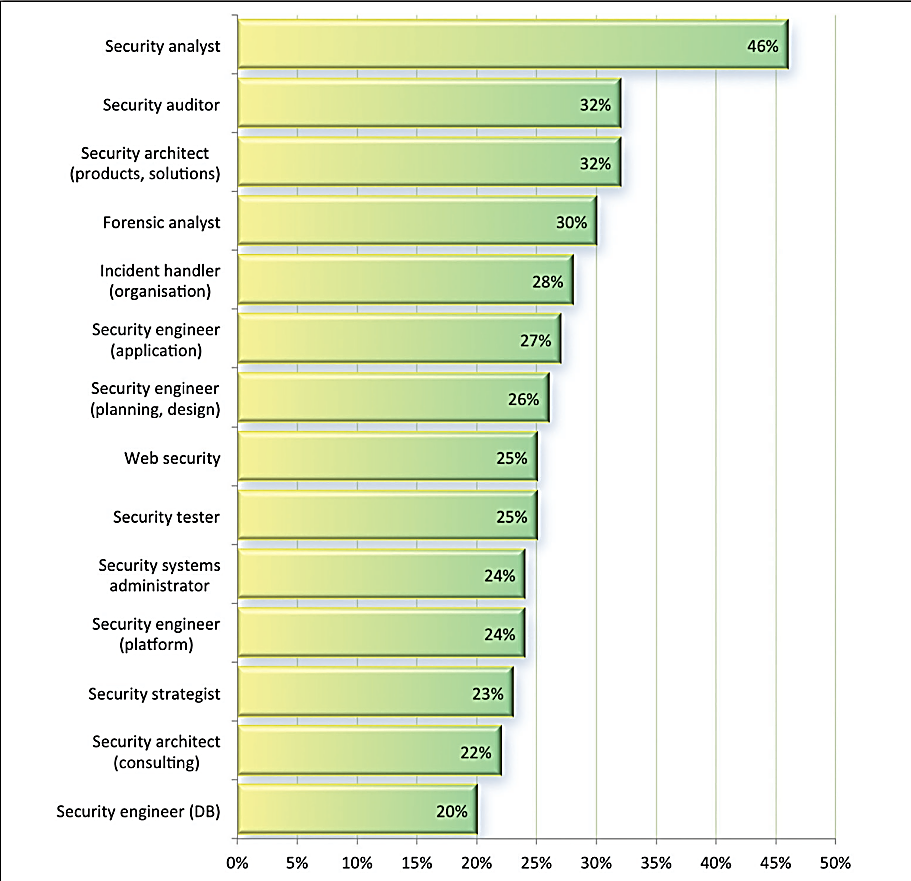
The ‘2015 Global Information Security Workforce Study’ from (ISC)2 found that 45% of organisations cited low availability of staff with the neces- sary security skills as a significant busi- ness problem.3 What’s more, a recent study from 451 Research found that the main issues encountered by secu- rity managers were lack of staff exper- tise (34.5%) and inadequate staffing (26.4%). UK research by KPMG also identified that more than half of the IT and HR executives surveyed would consider employing a hacker to provide information to the internal security teams – the main reason being that the
technical skills needed to prevent cyber- attacks vary substantially from those needed for every day IT security tasks.4 Ultimately in the current security land- scape, where threats are becoming more
advanced and sophisticated, the number of security professionals who can deal with these threats has not kept pace with demand.
What are the alternatives?
The difficulty of finding qualified pen- etration testers means that companies
vulnerability is identified, and the hack- ers have the opportunity to perfect their skills, elevate their reputation and in some cases even find employment.
“The company gets the economic advantage of only having to
pay when a vulnerability is identified and the hackers have the opportunity to perfect their skills, elevate their reputation and in some cases even find employment”
One risk of using the bug bounty method is that if the process is launched too early, the system is likely to be riddled with weaknesses and bugs. Typically, a bug that directly affects privacy or security is given a mini- mum monetary reward. For example,
Facebook offers a minimum of $500 to hackers for identifying weaknesses.5 Therefore, it is crucial for organisations
to ensure they have already addressed as many vulnerabilities as possible and have built a robust, secure and mature system. The bug bounty approach should be treated as the ultimate step in the secu- rity and quality assurance process, as it effectively invites all and sundry to poke around the operational systems. Failure to build robust systems will result in organisations essentially writing a blank cheque to all involved – or worse, quick- ly finding that operational systems have become non-operational.
The reasons behind the issue
So what is fuelling the lack of skilled security professionals, in particular pen- etration testers and ethical hackers? One reason may be the absence of education about cyber-security as a profession at tertiary institutions. In recent years the UK Government has launched a number of initiatives and is supporting university programmes in an attempt to combat the information security skills gap. But the market is unlikely to see much of an impact from this until more graduates enter the workforce in years to come.
One particular government strategy that was outlined at the recent Westminster
e-Forum about cyber-security was the for- mation of the new National Cyber Security Centre. This will see a public/private partnership formed with the Government Communications Headquarters (GCHQ), which will play a significant role in pro- moting the cyber-security industry and creating a stronger cyber environment for organisations across the EU. Essentially,
it will make it much simpler for the
Positions that organisations think are inadequately filled. Source: (ISC)2 GISWS.
Government to engage with industry on cyber-security related issues.
The industry impact
For security professionals who pos- sess the necessary skills and qualifica- tions, the opportunities are enormous.
According to global professional services consultancy Procorre, nearly 15% of cyber-security professionals earn at least
£100,000 a year.6 In some cases, an
experienced cyber-security expert can earn more than a chief security officer.
As the threat of data breaches contin- ues to grow for business across the globe, the role of penetration testers and ethical hackers is only going to become more important. This is especially true consid- ering that the IT security field is antici- pated to grow 37% by 2022. And while the need for penetration testing may once have resided purely in the domain of government departments, large organ- isations, multi-national corporations and financial institutions, it is now viewed
as an essential data security strategy for companies of all shapes and sizes.